4.3 Testing our Actions
1. Open your UI APP
2. Log out and Login again
Tip: In our previous challenge, we turned on MFA to be enforced in any login, you might want to turn it off again.
Tip: If you haven’t used our example user [email protected], now is the time to do so! Just sign up with that user rather than logging in with your existing user, the flow will work the same.
We need to login again as to trigger the actions during the login flow.
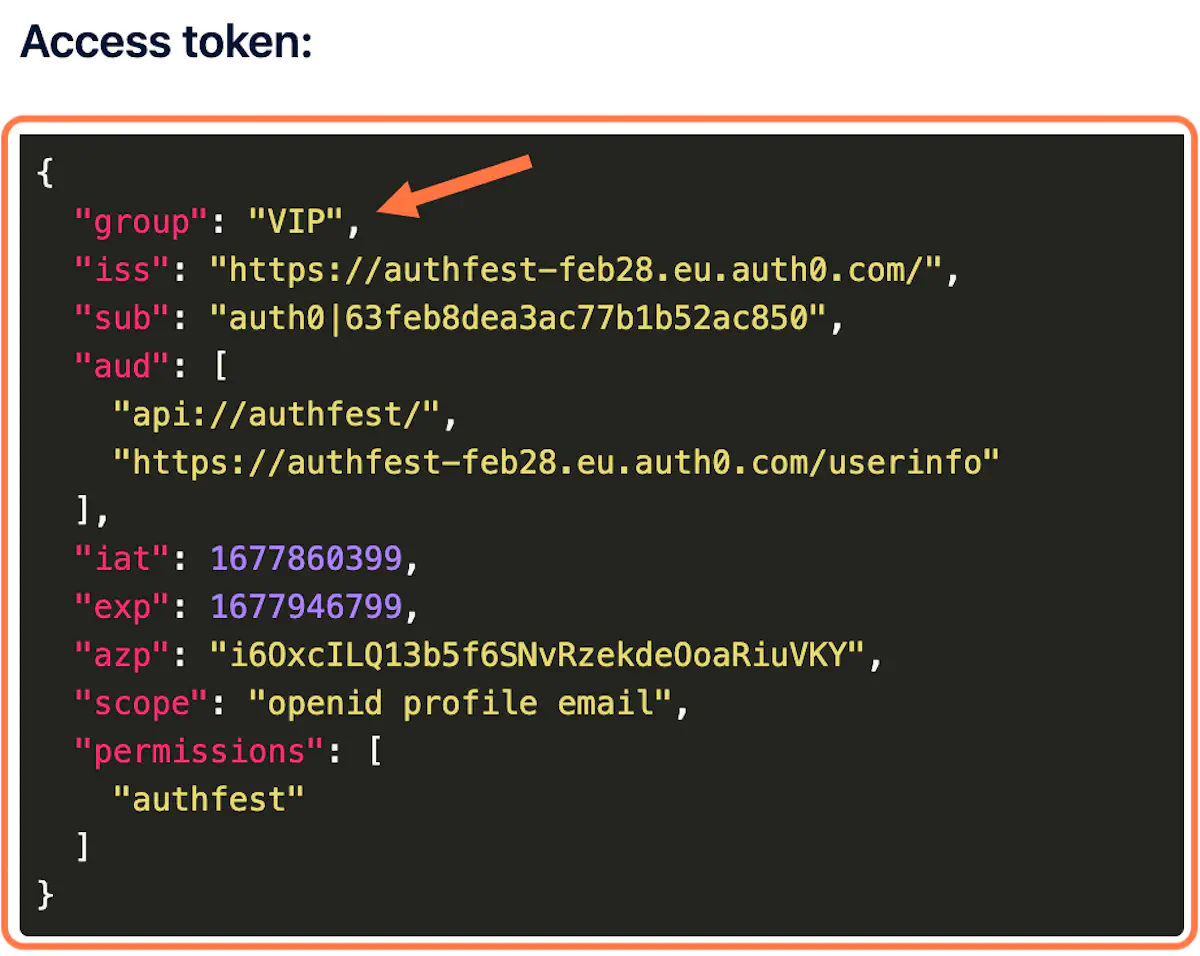
3. Check your Access Token
In the first action, we added the claim group. This was added as your user’s email belongs to the domain @authfest.com.
Extra challenge: Create a user with your personal email address, check what happens.
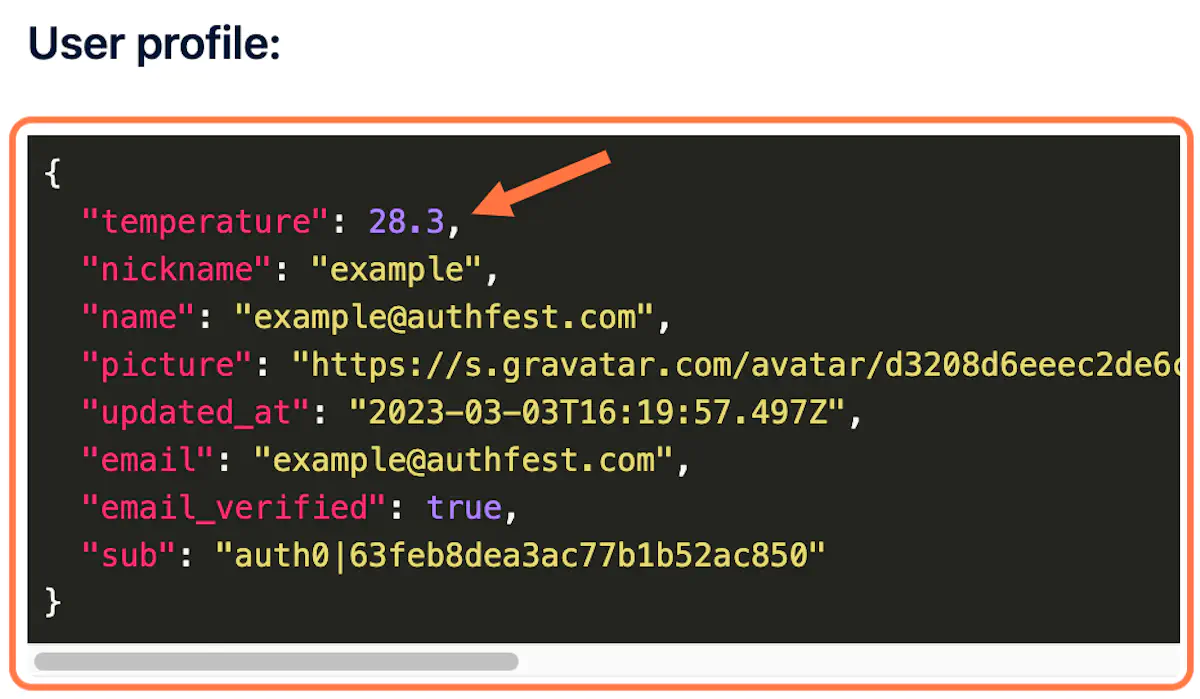
4. Check the ID Token
The second Auth0 action utilises the approximate latitude and longitude of the location where the login flow started. This location information is used to make a request to a public weather API. The API returns the current temperature in Celsius. Finally, this temperature information is added to the user’s ID token as a custom claim.
5. That’s a wrap!
You have successfully completed all of our training challenges. You have learned how to secure frontend and backend apps, enable MFA and create custom actions that allow you to extend the functionality of the platform.
We hope that these challenges have provided you with a valuable learning experience and have helped you to further understand the power of Okta’s CIC!
If you want to continue your learning check out our other developer labs: Auth0 Developer Labs