3.1 Test MFA
In this task, we will validate our new security policy by accessing the custom application.
- 1. Log in to your UI App
- 2. Scan the QR code with your Authenticator app (Google Authenticator, Microsoft Authenticator, etc.)
- 3. Add the 6 digit TOTP generated by your Authenticator app and continue
- 4. Congratulations, you’ve logged in!
- 5. Click on Logs
- 6. Search the entries related with your login
- 7. Go deeper and click on “Success Login”
- 8. Click on Context Data
On this page
- 1. Log in to your UI App
- 2. Scan the QR code with your Authenticator app (Google Authenticator, Microsoft Authenticator, etc.)
- 3. Add the 6 digit TOTP generated by your Authenticator app and continue
- 4. Congratulations, you’ve logged in!
- 5. Click on Logs
- 6. Search the entries related with your login
- 7. Go deeper and click on “Success Login”
- 8. Click on Context Data
1. Log in to your UI App
Use the same user as before. If you followed our example:
Email: [email protected]
Password: Authfest-2023
2. Scan the QR code with your Authenticator app (Google Authenticator, Microsoft Authenticator, etc.)
Since we’ve activated and are enforcing MFA every time, you will be requested to enroll in MFA as another factor of authentication.
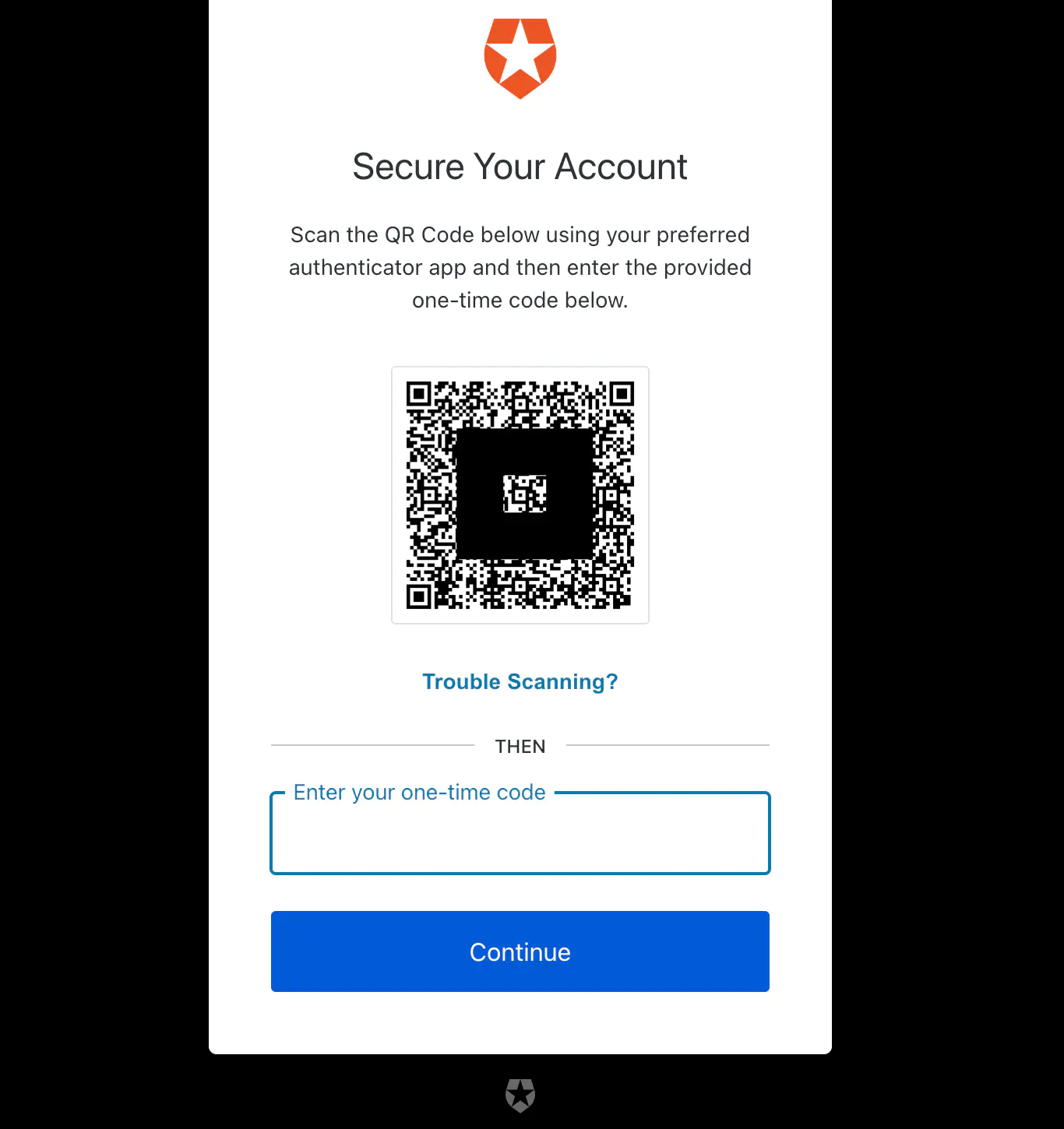
3. Add the 6 digit TOTP generated by your Authenticator app and continue
4. Congratulations, you’ve logged in!
Let’s have a look on how this was recorded in the CIC logs
5. Click on Logs
6. Search the entries related with your login
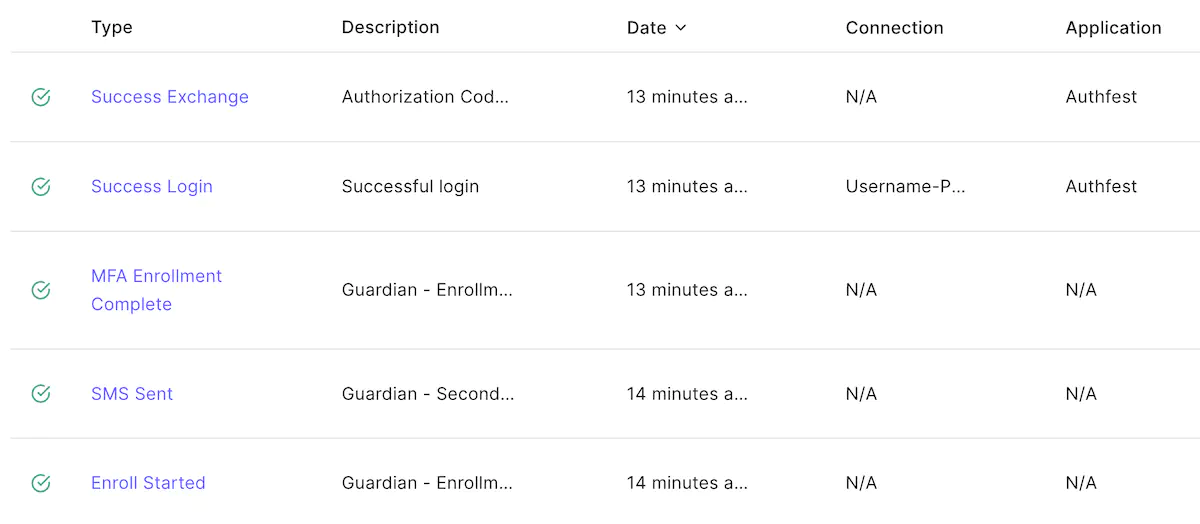
7. Go deeper and click on “Success Login”
This will present some details around the login flow

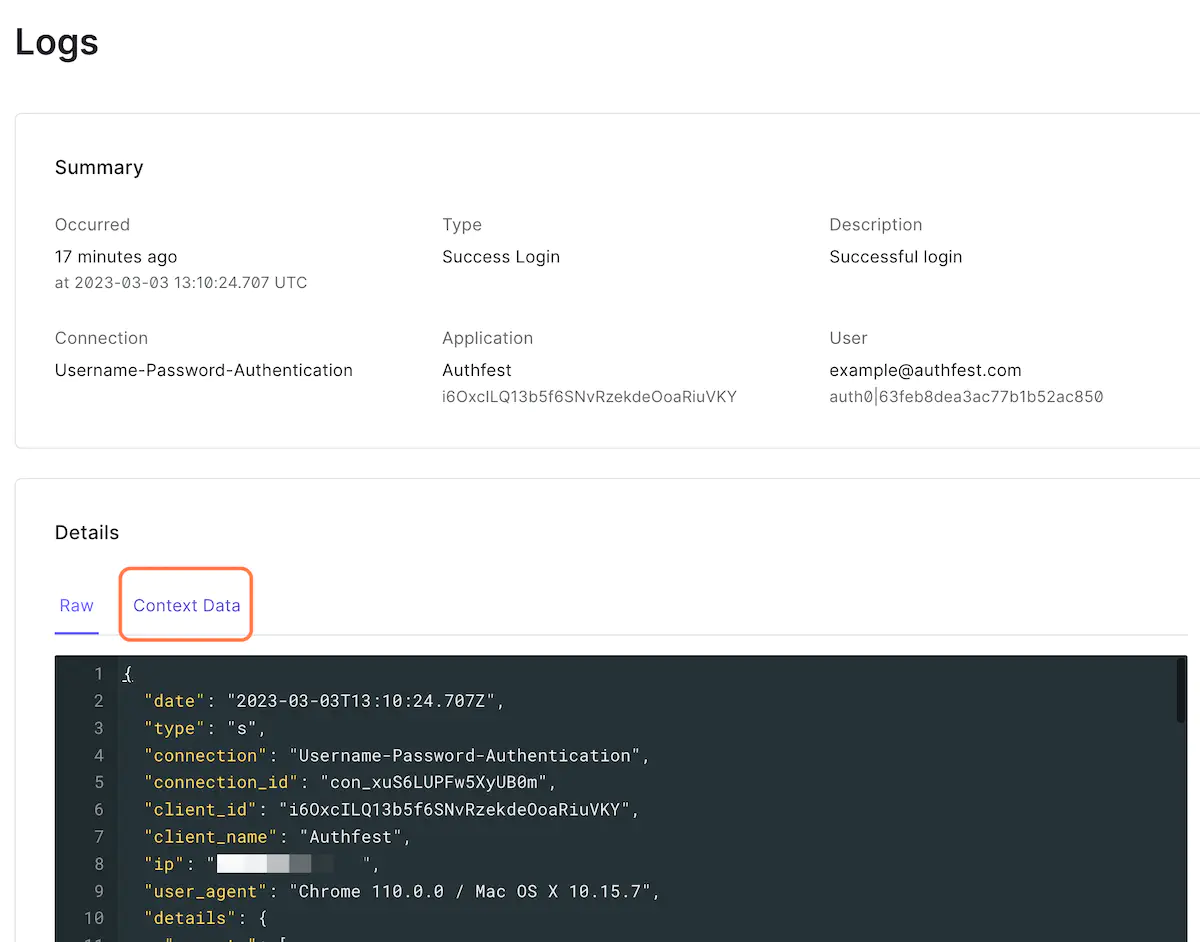
8. Click on Context Data
If you search deeper, you will find that mfa was triggered for this login flow.
This challenge strengthened the overall security of your application by adding multi-factor authentication. Since the application was already integrated with Okta CIC, a second level of authentication was implemented based on a policy without requiring any code changes.
You also got a glimpse into the Okta CIC log capabilities, allowing you to monitor for risk and stay on top of your tenants activity.